Can I use yubikey on chromebook?
I just installed 1Password X on my chromebook, can't see a way to use my yubikey. The only option I see is to use an app for MFA. Is there a way to use yubikey on my chromebook? tnx
1Password Version: Not Provided
Extension Version: 1.22.1
OS Version: ChromeOS 85.0.4183.133
Sync Type: Not Provided
Comments
-
Just to clarify, I want to use the yubikey to login to 1password, not for MFA on other sites.
Also, is there any way to edit a previous post, I don't see a way to do that. I'm using chrome on a chromebook.0 -
Hey @MarkL1 ,
I believe this will help you set up your YubiKey with your 1Password.com account: https://support.1password.com/security-key/
You can edit your messages on the forum here by hovering over them with your mouse, then clicking the little gear icon that shows up on the top right corner of the message. :chuffed:
0 -
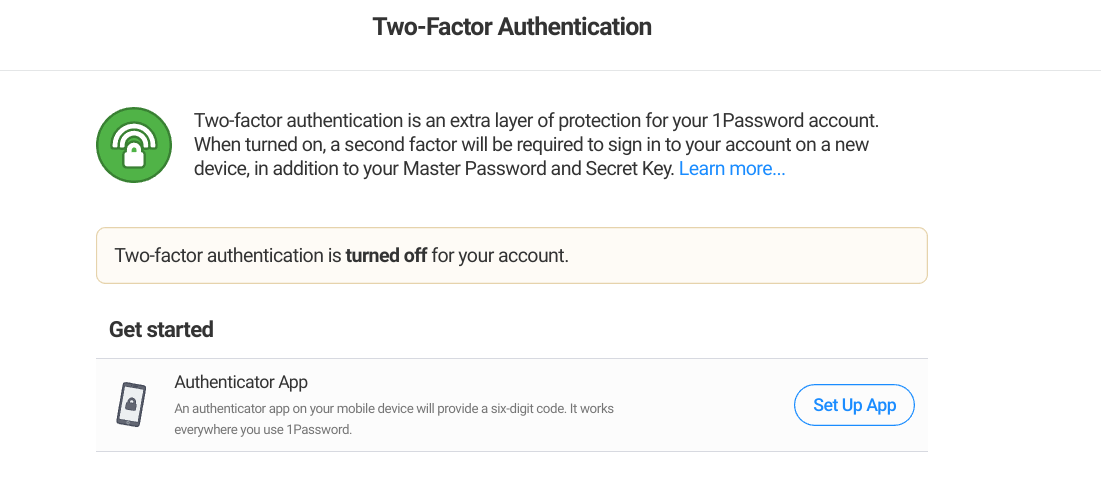
I had watched that video, but the screen choice in the video is different than what I'm presented with. I see the following screen, which indicates 2 factor authentication is turned off without offering any way to turn it on:
I noticed there is a time limit on editing a post, I was outside the 1 hour window when I tried to do the edit.
0 -
Currently not all clients support using Yubikeys for 2FA, so you'll need to use an OTP app so you can login to those clients (Windows, macOS).
iOS/Android/Web: you can use either the registered Yubikey or your registered authenticator app
Windows/macOS: can only use registered authenticator app0 -
I see the following screen, which indicates 2 factor authentication is turned off without offering any way to turn it on:
Please click on the Set Up App in the screenshot you posted to turn on 2FA :+1:
plttn is correct: after you set up an authenticator app, you will be able to setup a Yubikey too.
0 -
Please click on the Set Up App in the screenshot you posted to turn on 2FA :+1:
Thanks, I'll try that. I'm transitioning from lastpass and the only authenticator I've used was the lastpass authenticator, which I didn't like. I assume Google's authenticator is a good choice for chromebook and android.
0 -
OK, I installed google authenticator, went smooth. But now when I login to 1password I'm not prompted for a code, it allows me to login using only a password. Do I need to do something else to require the code for login? Here's the screen showing 2FA:
 0
0 -
2FA is only used by 1Password for the device authorization process. Once you've authorized a device, you won't be prompted for 2FA on that device again unless you deauthorize the device.
OK thanks, it's a different model than I'm used to. My concern has always been while I'm traveling that someone steals my laptop. With this model I can deauthorize the stolen device and will then force the thief to need 2FA to gain access to the kingdom.
0 -
Yes indeed you could. Deauthorizing the device would prevent any new data from being synced to it without entering the 2FA. However in that case if the thief were able to somehow obtain your Master Password from you they would be able to decrypt whatever data was already cached in 1Password prior to you deauthorizing the device. Your Master Password is what protects you in a stolen device situation, not 2FA. If you're concerned about that being a possibility, you would need to not only deauthorize the device, but then you would also need to change your passwords after doing so. You'd also want to change your Master Password, of course. :)
Ben
0 -
... Your Master Password is what protects you in a stolen device situation, not 2FA.
With my previous configuration using lastpass, if my laptop was stolen the vault would be inaccessible without the yubikey which was in my pocket, even if the thief knew the master password. That's one reason I liked that model, even though it was a bit of a pain to have to carry the yubikey all the time. I agree the first thing I would do in case of a stolen laptop now would be deauthorize it and change the master password as well as all my important account passwords just in case. If there are additional suggestions on how to handle that situation I'd be interested if you'd share them. I'm still learning the ins and outs of 1password.
Lastpass also had the concept of offline use, I haven't looked for that yet in 1password. I liked that when I was away from home because if I needed to access my vault I could access the local copy on my phone without sending my password or any traffic on the network.
0 -
Hey @MarkL1 ,
Using your YubiKey every time you want to unlock your password manager does indeed sound tiresome and not very user friendly. We'd rather protect your data with your Master Password for ease of use, while still maintaining your account's security and privacy.
If your device gets lost/stolen, your data is protected by your Master Password (unless it is written down/saved somewhere on that device in plain text). In any case, as Ben mentioned, the correct action in such a situation is to access your account from another device, deauthorize the lost/stolen device and change your Master Password (and Secret Key if you have reasons to believe that was compromised as well).
As for offline access - all of our native apps (for Mac, Windows, iPhone and Android) store a copy of your database on the device itself, so you can always use it even if you're offline (or even if we experience an outage on our servers). Your data is always accessible and our apps will keep on working. The only thing that won't work offline is syncing across devices, which will occur then ext time the device gets online.
Furthermore, your 1Password is unlocked locally and nothing important or unencrypted is being broadcast online when you unlock. You can learn more about our security methods and more in the following links:
0 -
Thanks for info. Now that I have an authenication app installed I tried to configure my yubikey again. I get the following error message each time I try to configure it:
 0
0 -
Nevermind, I tried a newer Yubikey and it worked. I'll retire the old one even though it works for other things.
0 -
Hey @MarkL1. I'm glad to hear that your newer YubiKey worked well for you. :smile:
0 -
FWIW. LastPass only really used the Yubikey for OTP not U2F, which means LP is not using a Yubikey the way many people think it is...
You might want to read this write-up:
https://pberba.github.io/security/2020/05/28/lastpass-phishing/One of the reasons I moved off of LP.
0 -
The older Yubikey most likely didn’t work because it predates U2F.
0 -
Thanks for the interesting read @robotarmy !
Quite interesting :)0




