hashcat, strong master passwords and changing your master password
Firstly, I have to applaud Jeff for both the considerable time and effort, and his attitude in writing his blog http://blog.agilebits.com/2013/04/16/1password-hashcat-strong-master-passwords/ and AgileBit's continued open attitude towards security.
The part I'm having difficulty with is here:
More recently, when a new keychain is created or the Master Password changed, we changed that to a minimum of 10000 iterations (and possibly more depending on your system).
I've been a customer for a couple of years, and I have an old keychain "encryptionKeys.js" with a couple of entries with "iterations":1000 inside. I'm guessing that the number 1000, refers to the number of PBKDF2 iterations performed.
So I changed my master password, and expected to see the number of iterations increase to 10000, but it stays at 1000. I'm using 1Password 3.8.20 on Mac, and I just expected the number of iterations to increase, as I'm sure I've read a couple of blog posts now saying that changing the master password increases the number of iterations on old keyfiles.
Is there another way to change the master password?
Comments
-
Hi @trammel,
I apologize for the confusion, we will clarify it in the blog post. The current 1Password 3.8.x users have to export their data and import into a new data file to increase their iterations count, changing the master password does not increase it by default. We'll look into fixing this in a future update.
The 3.9.x users at the Mac App Store does not have to do this, they just have to change their master password to increase the count.
To do this for your 1Password version, please do the following:
- Open the main 1Password app, go to the File Menu > Export All
- Save it in a safe isolated place, don't store it in any location that is backed up or synced like the Dropbox folder
- Create a new data file by following this instruction
- Once you unlock the new data file, import your data through the File Menu > Import, select 1Password Interchange File as the import source and then select the export file you created in Step 1-2.
You should be all set now. I hope that helps.
0 -
Hi, i have a comment and suggestions after reading the hashcat blog post:
You say, i quote:
" > The very first versions of the Agile Keychain Format long ago used 1000 PBKDF2 iterations...."
So why wasn't there a notification implemented in 1Password which told me to create a new master password - to update to the new format? Today i find out that i'm still using an "old format" even though i'm using the latest version of 1Password... that's obviously not good.Also, i want to suggest implementing a notification in the 1Password workflow to actually point users to the "Toward Better Master Passwords" blog post/information. Only computer geeks read the 1Password blog, the average 1Password user will never read/know this information. So it seems appropriate to point them to it.
Cheers.
0 -
Hi @Davide,
We did, it was in the changelog for 3.8.11 that shows up in the update notification. You can find it here: https://agilebits.com/onepassword/mac/release_notes#v31205
We agree, we need a better notification system, and we started experimenting with the News Feed option in the iOS app. We'll see if it works out better and if yes, we'll add it to the OS X.
0 -
Hi @Davide,
You are not alone in pointing out that we need to do more to help people pick better Master Passwords. You might want to take a look at this article:
http://emergentchaos.com/archives/2013/04/1password-hashcat.html
And thanks, @trammel for your correction. In my focus on some highly technical issues, I didn't address the behavior of anything other than 1Password 3.9. I'm hoping that we will have a more practical article for people to use. I would like to emphasize again that improving a Master Password gives you a much larger security gain than increasing the number of PBKDF2 iteration.
Cheers,
-j
–-
Jeffrey Goldberg
Chief Defender Against the Dark Arts @ AgileBits
http://agilebits.com0 -
First, thank you for the blog post on HashCat an making our pw's more secure.
I love your product very much but am kind of disapointed about the way the masterpw has to be structured to be really safe.
To make 1PW really safe I have to do enter a too long pw. period.
I bought 1PW to make my life easier not to enter mile long pw's. Not happy. I'm tech savy, but don't know how to communicate this to my 65 year old dad. Sorry. FAIL.0 -
Hi @Georg,
I understand, there's always a tradeoff when it comes to using a security product and using it for convenience.
In this case, you have to remember one strong master password to avoid remembering 100s of extra long passwords on various of websites in addition to encrypting the rest of your database.
I'm sure your dad would rather remember a 5-word passphrase than to remember each password for each site. A 5-word diceware passphrase or 11-character or more password would still take a million year to crack on a 2xGPU high-end system.
In a year or two, our new data format will be the standard, which improves the security strength of your master password by using newer and more intensive algorithms that will slow down the cracking rate.
Remember the same issue applies to any web services you use, you have to use a long password to protect your data on that service, or the same issue applies, they can brute force their way in if your password is too easy.
What's more important, the encryption of your data with one long password or having to remember all the different passwords without reusing the password once on any of the sites.
0 -
One thing I have always wondered about master passwords. How secure (or insecure) is something like choosing as password the first sentence of a favourite novel, or a line of Shakespeare?. I'm sure some of the brute force dictionaries will include the commonest such choices, but they can't include all possibilities.
0 -
Is there an error in your second chart in the blog post about hashcat? Seems like there shouldn't be two 193 years for 52 password strength entropy. Looking at the rest of the 2nd column showing 25000 PBKDF2, they all increase except for the row showing 52 entropy.
0 -
I'm sure some of the brute force dictionaries will include the commonest such choices, but they can't include all possibilities.
@danco: Choosing one that they do include is not really a risk worth taking especially when Diceware makes secure, memorable Master Passwords so easy to create. :)
Is there an error in your second chart in the blog post about hashcat? Seems like there shouldn't be two 193 years for 52 password strength entropy. Looking at the rest of the 2nd column showing 25000 PBKDF2, they all increase except for the row showing 52 entropy.
I've mentioned this to Jeffrey. Thanks for bringing it up, @millca.
0 -
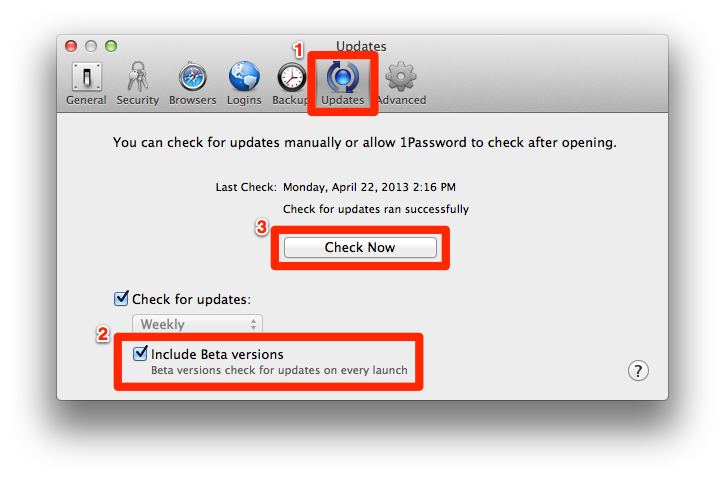
1Password 3.8.21.BETA-1 was just released with a change in this regard. From the release notes (emphasis added):
Increased the minimum number of PBKDF2 iterations when creating a new keychain and changing your Master Password.
Just check the box to "Include Beta versions" on the Updates preference pane and then click the "Check Now" button.
 0
0 -
Okay, thanks for your reply. I have another question/suggestion, will the 'dice method' described in the "Toward Better Master Passwords" blog be implemented in the 1Password Password Generator?
(something like http://simplestrongpasswordgenerator.com )And also, if there are still a lot of people who are using the old database format, why not automatically upgrade the database in a 1Password update?
0 -
I'm sure some of the brute force dictionaries will include the commonest such choices, but they can't include all possibilities.
@danco: Choosing one that they do include is not really a risk worth taking
Yes, I take your point. But I would like to have some idea of how much of that kind of info is in the brute force dictionaries.
My password isn't exactly such a phrase, but somewhat like it. I probably would not choose it if I was starting again, but don't feel inclined to change it if the risk is small. I'm trying to judge how much risk there is.
0 -
Okay, thanks for your reply. I have another question/suggestion, will the 'dice method' described in the "Toward Better Master Passwords" blog be implemented in the 1Password Password Generator? (something like http://simplestrongpasswordgenerator.com )
@Davide: It is certainly something we have thought about, but I can't give a time frame for when or if it will be implemented. I'll certainly pass your vote along. I think it would be great to have. :)
And also, if there are still a lot of people who are using the old database format, why not automatically upgrade the database in a 1Password update?
I'm not sure of the technical details, but this could be a possibility.
My password isn't exactly such a phrase, but somewhat like it. I probably would not choose it if I was starting again, but don't feel inclined to change it if the risk is small. I'm trying to judge how much risk there is.
@danco: With Diceware, the entropy is known and can be calculated. Jeff specifically discussed Kerckhoffs’ Principle when talking about creating good, strong Master Passwords. Folks should use a system for coming up with Master Passwords that doesn’t lose its strength if the attacker knows the system that was used. I'm not sure how you would calculate the entropy in a system like the one you describe, but if it isn't really random then I would be skeptical to use it myself. Humans are about as bad at being truly random as computers are at detecting patterns.
0 -
Care to comment on this development, Jeff? http://arstechnica.com/security/2013/08/thereisnofatebutwhatwemake-turbo-charged-cracking-comes-to-long-passwords/
0 -
I've seen some questions about passwords that are stored within 1Password. A 23 character password from 1Password's Strong Password Generator is already 128-bits. Hashcat isn't going to find those. As for your Master Password, I don't think anything has really changed from our post in April. But I think Jeff is working on a new post to confirm for folks that nothing has really changed. :)
0




