OpenSSL Heartbleed Bug
Comments
-
Is the advice you give on your blog ("Imagine no SSL encryption, it's scary if you try") true for 1Password3? (The advice being that 1Password4 is immune from Heartbleed)
I quote from http://help.agilebits.com/1Password3/security.html :
"1Password does not contain a single line of encryption code; instead we used OpenSSL, which is shipped with over 20 million Macs and is the standard used by most of the Internet. In addition to its huge user base, OpenSSL is open source. This is critical. It means that experts from around the world can view the code and ensure it is correct and does not contain any back doors [ed: :-O]."
I appreciate (if I understand correctly), that 1Password4 has moved away from OpenSSL for the new keychain format(?). Either that or Heartbleed is only relevant if it is running on a web server (not as a local encryption tool). I don't fully understand; please could you clarify?
Thanks,
Tom0 -
Hi @swiss68,
Like the 1Password app, the 1Password browser extensions are not affected by Heartbleed. There is no vulnerability in 1Password's encryption as a result of Heartbleed.
Only using 1PasswordAnywhere in your browser on Dropbox.com could have been vulnerable, as an attacker could possibly switch out the 1Password.html file for a malicious once that steals your Master Password. With that said, we do not believe that any attacks on 1PasswordAnywhere took place, but we can't rule it out for sure.
And regardless of using 1PasswordAnywhere, it's definitely a good idea change your Dropbox password.
Hi @tommy_tipper,
You're right, 1Password 3 did use OpenSSL, but Heartbleed exploited the heartbeat extension in OpenSSL, and no version of 1Password ever relied on that. The short version is that there is no vulnerability in 1Password's encryption as a result of Heartbleed.
For more details, please see @jpgoldberg's post here.
0 -
I'm getting pretty disgusted with 1PW on this issue...the silence is deafening.
Time to move to Last Pass, i think...
0 -
I appreciate (if I understand correctly), that 1Password4 has moved away from OpenSSL for the new keychain format(?).
The data format and the crypto libraries we use are separate questions. We had moved away from the OpenSSL crypto libraries years before we move to the new data format. It doesn't matter for the format whether we use PBKDF2 in OpenSSL or in CommonCrypto. For clarification on this (and some history) do take a look at that post of mine which @JasperP mentioned.
(It's not entirely true that data format and choice of crypto libraries are entirely separate questions. Had we gone back of OpenSSL, we would have been able to use a more efficient form of authenticated encryption in the new format than we decided on. Encrypt-then-MAC (which we use) is slow as it requires two passes over the data, but other authentication encryption modes weren't fully supported in CommonCrypto when we made our design choice.)
Either that or Heartbleed is only relevant if it is running on a web server (not as a local encryption tool).
As always, things are more complicated. Heartbleed matters for things talking SSL. Typically that is servers. But when browsers talk to SSL servers, then they, too, are talking SSL. So some web browsers or SSL clients have also been affected. But in general you are correct. This is not about local encryption tools. SSL is a communications protocol, and the bug is in how part of that protocol is implemented. It makes it possible to extract information from a server that should not be extracted.
0 -
By the way, we're working on integrating our new Watchtower service into the main 1Password app. This is now available in the latest 4.3.1 beta 1:
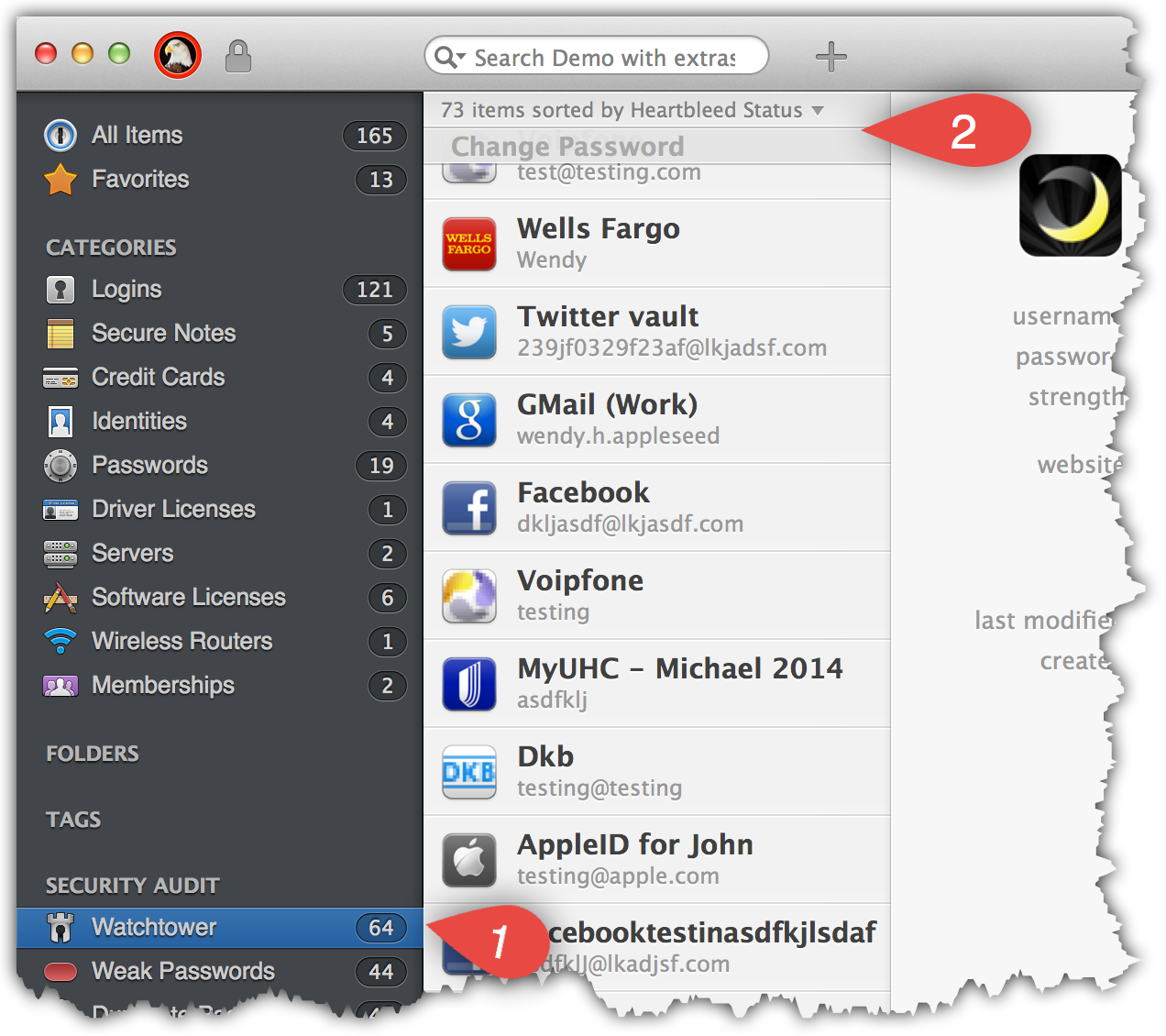 0
0 -
Confusing tool.
- The Security Audit tool has only two categories versus the five in the online Watchtower test.
- "Not Vulnerable" in the Security Audit tool means something very different than "Not Vulnerable" in the online test.
- The Security Audit tool does not tell the user why a password change is recommended. Does this matter? Yes, IMO, because the reason affects prioritization.
Looking forward to evolution.
0 -
Hmm. I just upgraded to the beta and see the activation option. However, it simply "unclicks" itself immediately. I may have screwed something up by accidentally starting an old non-beta (4.1) after that ... not sure what to do now.
0 -
Please see the existing threads in the 1Password 4 for Mac Beta category and this one in particular for that issue:
4.3.1.BETA-1: Watchtower will not enable [Confirmed, will fix in the next beta update]
Please keep the feedback coming! The beta category is the perfect place for more. :)
0 -
Will v4.3.1 correct the 1Password Anywhere OpenSSL dependency? You guys are really awesome. You've got transparent information about where your holes are, and you are telling us exactly what you doing to address it. Head and shoulders above mates... head and shoulders.
0 -
1PasswordAnywhere itself does not rely on OpenSSL. But since it is accessed via Dropbox.com (which was vulnerable to Heartbleed), we temporarily recommended not to use it. Dropbox.com is now patched, and you can go back to using 1PasswordAnywhere! :)
Please let us know if you have any other questions!
0





