Feature Request: autofill one time passwords via yubikey
The advantage of storing time-based one time passwords (2fa TOTPs, the ones traditionally used in Google Authenticator) in 1Password is that it's convenient to let 1Password autofill the 2fa field.
However, some threat models arguably require users to physically separate their passwords from their second factor; in my case I've done this via a Yubikey.
Yubikeys store (up to 21 or something?) TOTP secrets. As is typical with smartcards, a computer can request that the key generate one token but cannot extract the secret (the one used to generate codes) from the key. Although there may be various attacks involving lying to the chip regarding the current time, using a Yubikey for generating TOTP codes is very convenient and arguably more secure assuming honest hosts.
If 1Password allowed users to autofill one-time passwords through a yubikey, they would be able to combine the convenience of 1Password autofill with the security benefit of using a physical, separate second factor device to authenticate.
I understand that this might be difficult to explain to users, however, so I understand if it is not implemented. It would be really nice to have, though :smile:
1Password Version: Not Provided
Extension Version: Not Provided
OS Version: Not Provided
Sync Type: Not Provided
Comments
-
Hi @InnocentVillain,
I don't know Yubikey well at all but I believe some of my colleagues have more experience. A bit of Googling suggested certain Yubikeys present themselves as a keyboard and pressing a hardware button causes the device to "type" the current code. I assume something you've seen indicates that there is a Yubikey API which can be used to query the device if present and request the current code, would that be a reasonable understanding?
0 -
While researching my answer, I found a similar feature request on this forum (i.e. this question would be considered a duplicate). I'll provide what I did find below, however.
Yubikeys offer their own HOTP (hash-based one-time password) system in addition to implementing the TOTP protocol we commonly see (i.e. the one used by google, github, 1password, etc).
Although their HOTP system sends its output to its host via the USB keyboard protocol, TOTP is accessed through either USB via CCID or NFC via ISO 7816-4.
Yubico's documentation includes both a general overview and the technical specs of the protocol.
I assume something you've seen indicates that there is a Yubikey API which can be used to query the device if present and request the current code, would that be a reasonable understanding?
This is my understanding, yes. Yubico provides a (very high-level) graphic of this in the documentation hyperlinked above:
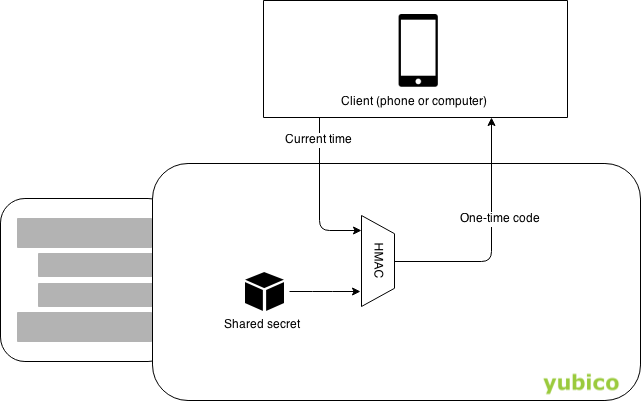
Yubico provides open-source clients for android and desktop. I assume that an iOS client is available, but as you know, it's dangerous to assume :wink:
0 -
Similarly, it's probably best not to assume that this would be a good idea in the first place. It also seems a bit circuitous to involve 1Password at all when Yubikey offers this function itself, so I'm not sure what the benefit would be. And 1Password would need to account for failure states where the device was not present or unresponsive. It's really simpler if 1Password has the data itself so that it can not only utilize it, but also safeguard it. Certainly something we can consider for the future, but taking input/code from a 3rd party is also never something to be done lightly. Cheers! :)
0
